Download CompTIA PenTest+ Certification Exam.PT1-002.ExamTopics.2025-08-07.107q.vcex
| Vendor: | CompTIA |
| Exam Code: | PT1-002 |
| Exam Name: | CompTIA PenTest+ Certification Exam |
| Date: | Aug 07, 2025 |
| File Size: | 206 KB |
| Downloads: | 4 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
A penetration tester writes the following script:
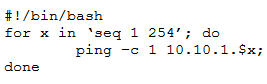
Which of the following objectives is the tester attempting to achieve?
- Determine active hosts on the network.
- Set the TTL of ping packets for stealth.
- Fill the ARP table of the networked devices.
- Scan the system on the most used ports.
Correct answer: A
Explanation:
A: 1 - Mosted A: 1 - Mosted
Question 2
User credentials were captured from a database during an assessment and cracked using rainbow tables. Based on the ease of compromise, which of the following algorithms was MOST likely used to store the passwords in the database?
- MD5
- bcrypt
- SHA-1
- PBKDF2
Correct answer: A
Explanation:
A: 1 - MostedReference:https://www.geeksforgeeks.org/understanding-rainbow-table-attack/ A: 1 - Mosted
Reference:
https://www.geeksforgeeks.org/understanding-rainbow-table-attack/
Question 3
Running a vulnerability scanner on a hybrid network segment that includes general IT servers and industrial control systems:
- will reveal vulnerabilities in the Modbus protocol.
- may cause unintended failures in control systems.
- may reduce the true positive rate of findings.
- will create a denial-of-service condition on the IP networks.
Correct answer: B
Explanation:
B: 1 - MostedReference:https://www.hsdl.org/?view&did=7262 B: 1 - Mosted
Reference:
https://www.hsdl.org/?view&did=7262
Question 4
An Nmap network scan has found five open ports with identified services. Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
- OpenVAS
- Drozer
- Burp Suite
- OWASP ZAP
Correct answer: A
Explanation:
A: 1 - MostedReference:https://pentest-tools.com/network-vulnerability-scanning/network-security-scanner-online-openvas A: 1 - Mosted
Reference:
https://pentest-tools.com/network-vulnerability-scanning/network-security-scanner-online-openvas
Question 5
Performing a penetration test against an environment with SCADA devices brings additional safety risk because the:
- devices produce more heat and consume more power.
- devices are obsolete and are no longer available for replacement.
- protocols are more difficult to understand.
- devices may cause physical world effects.
Correct answer: D
Explanation:
C: 2D: 7 - Mosted C: 2D: 7 - Mosted
Question 6
When developing a shell script intended for interpretation in Bash, the interpreter /bin/bash should be explicitly specified. Which of the following character combinations should be used on the first line of the script to accomplish this goal?
- <#
- <$
- ##
- #$
- #!
Correct answer: E
Explanation:
E: 9 - Mosted E: 9 - Mosted
Question 7
A new security firm is onboarding its first client. The client only allowed testing over the weekend and needed the results Monday morning. However, the assessment team was not able to access the environment as expected until Monday. Which of the following should the security company have acquired BEFORE the start of the assessment?
- A signed statement of work
- The correct user accounts and associated passwords
- The expected time frame of the assessment
- The proper emergency contacts for the client
Correct answer: D
Explanation:
A: 2B: 4C: 3D: 21 - Mosted A: 2B: 4C: 3D: 21 - Mosted
Question 8
A security engineer identified a new server on the network and wants to scan the host to determine if it is running an approved version of Linux and a patched version of Apache. Which of the following commands will accomplish this task?
- nmap ג€"f ג€"sV ג€"p80 192.168.1.20
- nmap ג€"sS ג€"sL ג€"p80 192.168.1.20
- nmap ג€"A ג€"T4 ג€"p80 192.168.1.20
- nmap ג€"O ג€"v ג€"p80 192.168.1.20
Correct answer: C
Explanation:
C: 3 - Mosted C: 3 - Mosted
Question 9
Which of the following should a penetration tester do NEXT after identifying that an application being tested has already been compromised with malware?
- Analyze the malware to see what it does.
- Collect the proper evidence and then remove the malware.
- Do a root-cause analysis to find out how the malware got in.
- Remove the malware immediately.
- Stop the assessment and inform the emergency contact.
Correct answer: E
Explanation:
B: 1E: 7 - Mosted B: 1E: 7 - Mosted
Question 10
A penetration tester wants to identify CVEs that can be leveraged to gain execution on a Linux server that has an SSHD running. Which of the following would BEST support this task?
- Run nmap with the ג€"o, -p22, and ג€"sC options set against the target
- Run nmap with the ג€"sV and ג€"p22 options set against the target
- Run nmap with the --script vulners option set against the target
- Run nmap with the ג€"sA option set against the target
Correct answer: C
Explanation:
A: 3B: 1C: 10 - MostedD: 1 A: 3B: 1C: 10 - MostedD: 1
Question 11
During a penetration-testing engagement, a consultant performs reconnaissance of a client to identify potential targets for a phishing campaign. Which of the following would allow the consultant to retrieve email addresses for technical and billing contacts quickly, without triggering any of the client's cybersecurity tools?
(Choose two.)
- Scraping social media sites
- Using the WHOIS lookup tool
- Crawling the client's website
- Phishing company employees
- Utilizing DNS lookup tools
- Conducting wardriving near the client facility
Correct answer: AC
Explanation:
AB: 2AC: 11 - Mosted AB: 2AC: 11 - Mosted
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!




